Difference between revisions of "Open Control Architecture"
| (12 intermediate revisions by the same user not shown) | |||
| Line 54: | Line 54: | ||
== Communications == | == Communications == | ||
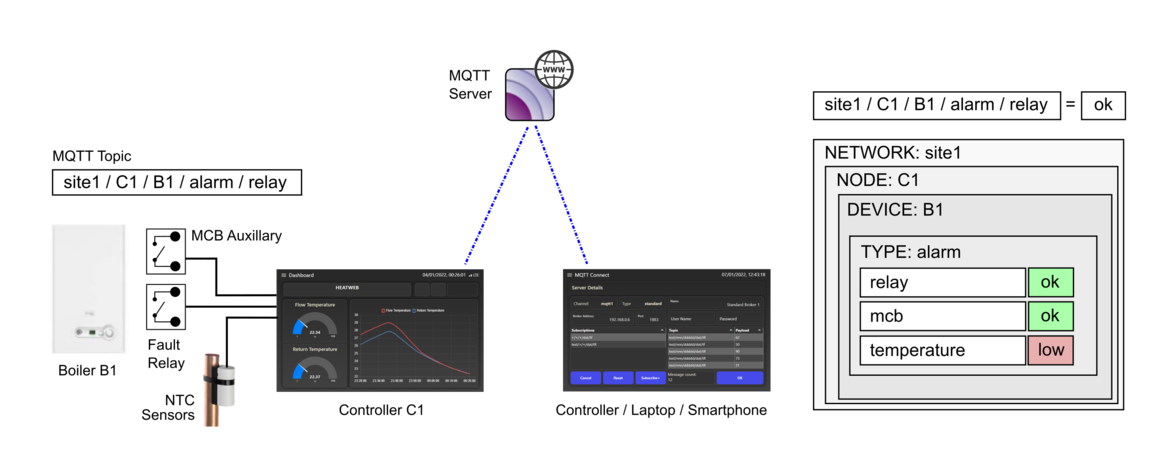
{{Block |A standardised 5 level MQTT topic structure is used throughout. '''''network''' / '''node''' / '''device''' / ''' | {{Block |A standardised 5 level MQTT topic structure is used throughout. '''''network''' / '''node''' / '''device''' / '''vargroup''' / '''varkey'''.'' | ||
<br>See https://github.com/heatweb/heat-network}} | <br>See https://github.com/heatweb/heat-network}} | ||
[[File:Bmscoms1.png|center|frameless|1176x1176px]] | [[File:Bmscoms1.png|center|frameless|1176x1176px]] | ||
| Line 100: | Line 100: | ||
== Data Groups == | == Data Groups == | ||
{{Block | The topic group (4th level ) is used to define the type of data. Values include: | {{Block | The topic group (''vargroup'') (4th level) is used to define the type of data. Values include: | ||
*'''''dat''''' (operational data) | *'''''dat''''' (operational data) | ||
*'''''stat''''' (statistics and status) | *'''''stat''''' (statistics and status) | ||
| Line 164: | Line 164: | ||
== Security and Access Control == | == Security and Access Control == | ||
{{Block |Each MQTT Broker runs its own security settings, with a list of users and associated topic permissions (read & write). Additional bridges enables data between MQTT brokers to be managed, and allows common user/password lists to be utilised. Password lists are based on hashed passwords (one way encryption) so that original passwords are never known or shared.}} | {{Block |Each MQTT Broker runs its own security settings, with a list of users and associated topic permissions (read & write). Additional bridges enables data between MQTT brokers to be managed, and allows common user/password lists to be utilised. Password lists are based on hashed passwords (one way encryption) so that original passwords are never known or shared.}} | ||
{{Block |Devices within a local network (LAN) can be protected using standard firewall rules with port forwarding used to expose MQTT services as required. Pulling all data and communications through MQTT allows all other external routes to be more easily locked down, with only secure MQTT ports to the LAN Broker exposed online. In this way external access is completely ruled by the same MQTT users and password structure.}} | {{Block |Devices within a local network (LAN) can be protected using standard firewall rules with port forwarding used to expose MQTT services as required. Pulling all data and communications through MQTT allows all other external routes to be more easily locked down, with only secure MQTT ports to the LAN Broker exposed online. In this way external access is completely ruled by the same MQTT users and password structure.}} | ||
{{Block |User access rules are stored in an '''ACL File''', with the following powers: | {{Block |User access rules are stored in an '''ACL File''', with the following powers: | ||
| Line 171: | Line 170: | ||
* Wildcards can be applied to rules, on any of the topic levels. This allows, for example, a particular user to be given access to '''''myNetwork/+/+/meter/#''''' providing access to meter data from ''myNetwork'', all nodes and devices. | * Wildcards can be applied to rules, on any of the topic levels. This allows, for example, a particular user to be given access to '''''myNetwork/+/+/meter/#''''' providing access to meter data from ''myNetwork'', all nodes and devices. | ||
* General rules can be setup for all users, providing global data. | * General rules can be setup for all users, providing global data. | ||
* Rules can include special fields, such as the MQTT client id or username. This allows general rules to be setup that, for example, '''''+/+/%u/cmd/#''''' provide nodes with read access to commands directed at them. }} | * Rules can include special fields, such as the MQTT client id or username. This allows general rules to be setup that, for example, '''''+/+/%u/cmd/#''''' provide nodes with read access to commands directed at them. }}{{Block |As MQTT can transport any form of data at high speed, including raw buffers, many insecure serial communications protocols, including Modbus and M-Bus can be piped via MQTT topics, rather than expose them directly. This pulls access to the data into the common rules. }} | ||
Separate read topic and write topic are used, for example: | |||
'''''myNetwork/+/n5hsi72k/modbus/request''''' | |||
'''''myNetwork/n5hsi72k/n5hsi72k/modbus/response''''' | |||
Likewise, the transparent M-Bus port on an Elvaco CMe3000 could be piped over: | |||
'''''myNetwork/+/cme3000/mbus/request''''' | |||
'''''myNetwork/n5hsi72k/cme3000/mbus/response''''' | |||
It would however be more normal to convert bus data such as this into individual topics for each register or field and expose these through MQTT to provide more granular control over access, remove the need for remote handling, and add report by exception rules (rather than keep continuously fetching values to catch a change). | |||
== Data Attributes == | == Data Attributes == | ||
{{Block |Attributes (metadata) provide additional information about data, such as units and a description. They include: | {{Block |Attributes (metadata) provide additional information about data, such as units and a description. They include: | ||
| Line 245: | Line 252: | ||
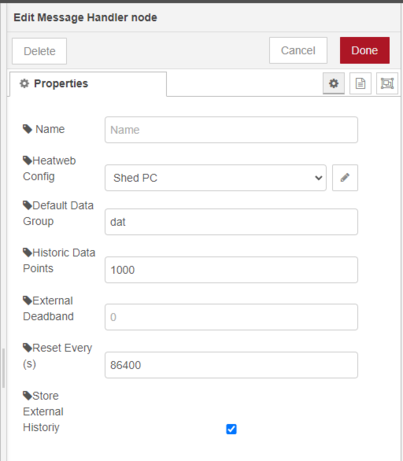
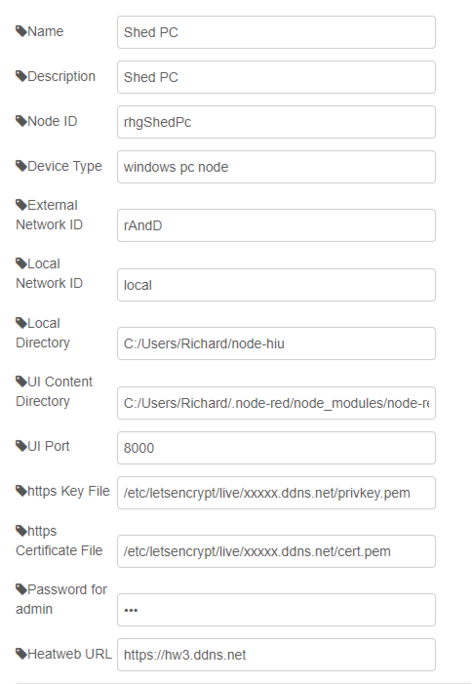
[[File:Settings3.png]]{{Block | Persistent settings for local devices are held on disk and in the '''''global.deviceSettings''''' object, and are specific to a device (or node).}} | [[File:Settings3.png]]{{Block | Persistent settings for local devices are held on disk and in the '''''global.deviceSettings''''' object, and are specific to a device (or node).}} | ||
== Links == | |||
* https://github.com/mcci-catena/docker-iot-dashboard A GitHub project using similar architecture for monitoring LoRaWAN devices. | |||
Latest revision as of 01:17, 29 November 2022
Basic Architecture
- Real-time global commutation (<0.5s latency) of any payload type between millions of devices
- Open source and licence free for life
- Battle hardened, standard and secure technologies
- Simple to use for plumbers and electricians
- Can connect to anything, physical or web based, and make use of commercial services and APIs
- Implement a standard dictionary structure to enable interoperability between systems
We have chosen to base the Open Controls Architecture on Node-RED for a number of reasons:
- Open source and free to use at will
- Cross platform, from PCs, to cloud servers to embedded devices, the Raspberry Pi, and many industrial PLCs
- Very stable, having been actively developed for over 10 years with the likes of IBM
- Simple to use with a visual interface that compares to electrical wiring
- Software can be copied and pasted from one system to another, dropped in and wired up
- Infinitely versatile with standard and custom components available from an online library to achieve almost any function or connect to any system
- Complex software can be built in a hurry, dragging components in and wiring up, then refined and packaged into neat and updateable components
- Built on Node.js and JavaScript, possible the world's most active software environment as used on all web pages
- Used by almost everyone - from hobbyists through to mobile phone companies - with considerable community support
- Provides a means to easily implement new and existing technologies and online services, including machine learning, peer-to-peer communications, databases, and encryption
Node-RED version 2 (or higher) is required for the latest active MQTT management.
- node-red-contrib-heatweb provides a set of nodes to implement the protocols used on this site
- node-red-dashboard provides a live user interface
- node-red-node-email provides email functions
Other Nodes are used, and can be installed as required.
A node can be:
- a function block within Node-RED (a Node-RED Node)
- an instance of Node-RED (a Controller Node)
- any point in the communications network (e.g. an MQTT Broker)
- Only letters and numbers should ever be used in naming.
- Dashes (-) may be used to create hierarchy as described below
- Underscores ( _ ) can be used at a software level, to add functionality, but not at an operational or user level.
- Spaces, full stops, commas, apostrophes, or any special characters must NEVER be used in naming.
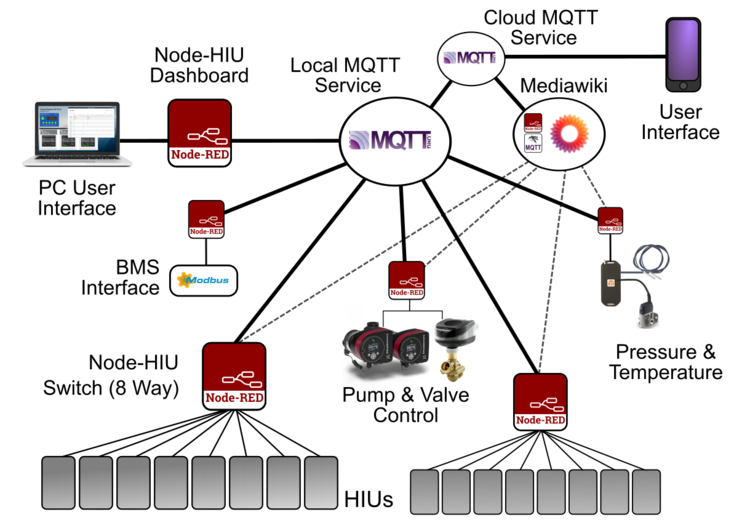
Communications
See https://github.com/heatweb/heat-network
This must be unique (long) and without spaces.
myNetwork/plantroomNode/plantroomNode/settings/title = "Main Plantroom Controller"
block1/blk1node/blk1node/settings/title = "Block 1 Controller" !!! DO NOT USE COMMON NETWORK IDs
Adding a prefix to sub-networks ensures networks remain unique on a higher level server. E.g. There may be two unconnected networks with sub-networks called "block1".
myNetwork-block1/blk1node/blk1node/settings/title = "Block 1 Controller"
anotherNetwork-block1/blk1node/blk1node/settings/title = "Block 1 Controller"
e.g. Ea5lQXfF2tmBlzYk
Nodes should also be given unique identities. Nodes Id's can be shorter as they only need to be unique within a network, rather than globally (in the whole world).
e.g. jxt15EwkThe titles of networks, as well as nodes, can be saved and found under its device setting.
Ea5lQXfF2tmBlzYk/jxt15Ewk/network/settings/title = "My Heat Network"
Ea5lQXfF2tmBlzYk/jxt15Ewk/jxt15Ewk/settings/title = "Main Plantroom Controller"
And to simplify for sub-nodes it is possible to use a node's id as the node's network identifier.
a5lQXfF2tmBlzYk-fg4jS8s7/fg4jS8s7/network/settings/title = "Block 1 Heat Network"
a5lQXfF2tmBlzYk-fg4jS8s7/fg4jS8s7/fg4jS8s7/settings/title = "Block 1 Controller"
a5lQXfF2tmBlzYk-fg4jS8s7-nnf555dE/nnf555dE/nnf555dE/settings/title = "Block 1, Flat 17 Controller"
Data Groups
- dat (operational data)
- stat (statistics and status)
- settings (persistent settings)
- cmd (a command)
- set (command to change a setting)
- system (software and networking)
- meter (meter data)
- alarm (alarms and warnings)
- ana (analogue readings)
- json (JSON formatted data)
- modbus (Modbus serial data)
- design (preloaded design data)
- TIL (Thermal Integration Ltd.)
- PCDB (SAP Product Characteristics Database)
- BENCHMARK (Benchmark information)
Manufacturer specific data groups can be used by systems to load a manufacturer's default data attributes, enabling the protocol to be extended as required.
They allow, for example, multiple organisations to publish the same data on a device (such as a heat network) without collisions.
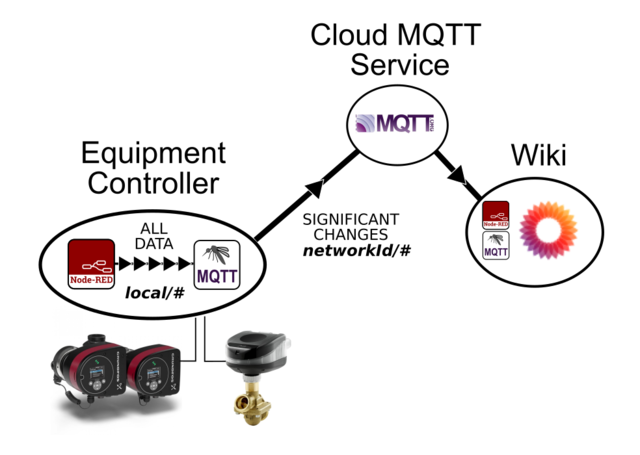
Handling Data
- The Node has two outputs - one for local traffic, and one for external traffic.
- Report by exception rules are applied to external traffic.
- The Node formats topics to the five level standard, adding group and device if missing.
- The Node stores data into global.readings, along with any attributes within the incoming message, as well as timestamps.
- The Node stores historical data into global.readingsHistory, along with timestamps, removing repeat values.
- New attributes are read from incoming messages, and existing attributes added to outgoing traffic.
- Handles the set data group, altering settings and saving to disk.
- Handles the json/sync topic, updating stored device readings and attributes to incoming sync data.
- Handles the cmd/sync topic, sending stored device readings and attributes as JSON.
- Handles the cmd/request topic, sending stored data as per requests.
- Additional routing can be performed within Node-RED, including selection of retained vs unretained routes.
Handler Nodes use a configuration node to store setup information including network and node identities.
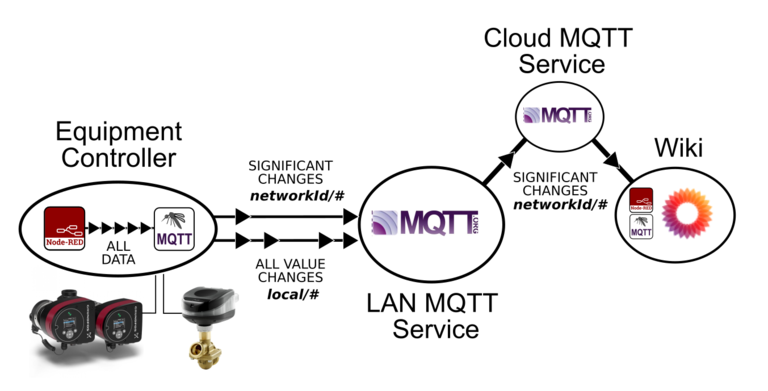
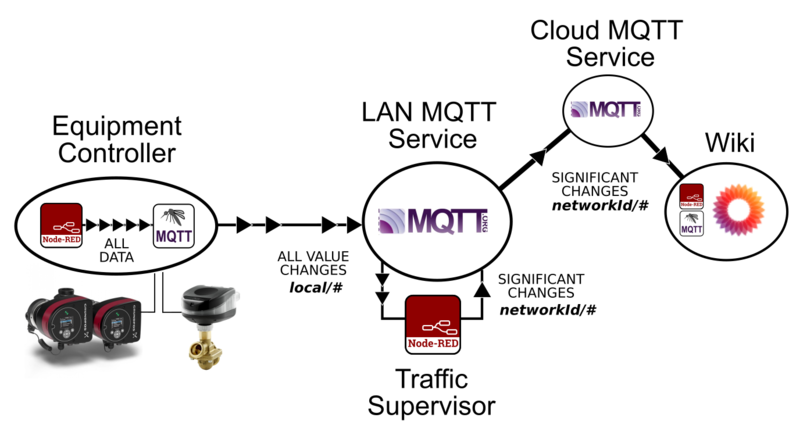
Routing Data
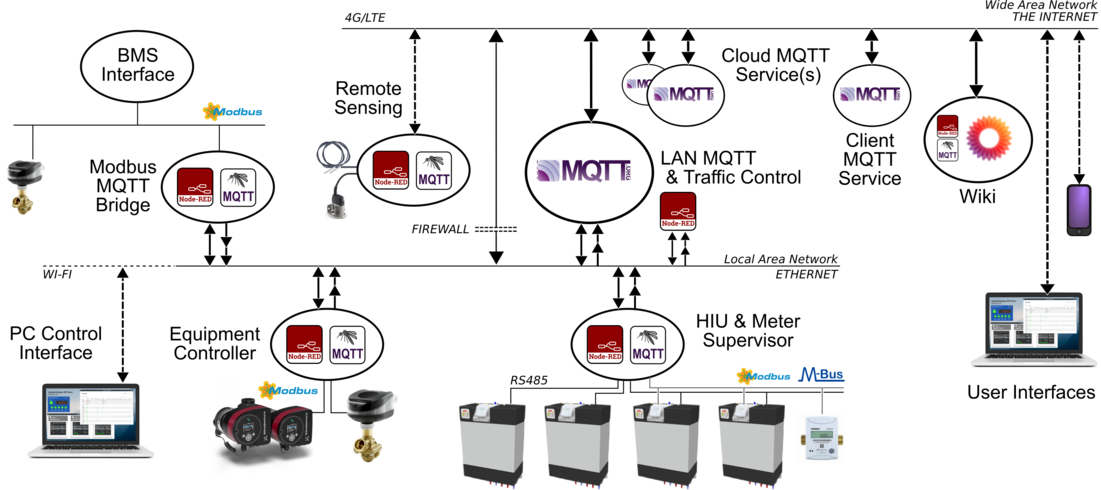
Complex Architecture
Security and Access Control
- Access rules can be applied to read and write permissions separately.
- Wildcards can be applied to rules, on any of the topic levels. This allows, for example, a particular user to be given access to myNetwork/+/+/meter/# providing access to meter data from myNetwork, all nodes and devices.
- General rules can be setup for all users, providing global data.
- Rules can include special fields, such as the MQTT client id or username. This allows general rules to be setup that, for example, +/+/%u/cmd/# provide nodes with read access to commands directed at them.
Separate read topic and write topic are used, for example:
myNetwork/+/n5hsi72k/modbus/request myNetwork/n5hsi72k/n5hsi72k/modbus/response
Likewise, the transparent M-Bus port on an Elvaco CMe3000 could be piped over:
myNetwork/+/cme3000/mbus/request myNetwork/n5hsi72k/cme3000/mbus/response
It would however be more normal to convert bus data such as this into individual topics for each register or field and expose these through MQTT to provide more granular control over access, remove the need for remote handling, and add report by exception rules (rather than keep continuously fetching values to catch a change).
Data Attributes
- units (units for data)
- title (short description)
- points (maximum data points to store in history)
- deadband (the deadband used for external communications)
- timestamp (unix time data is generated or handled)
- changed (unix time data last changed)
- attributes (an object containing custom attributes)
The flow below shows a message object, with attributes, before and after going through an MQTT connector.
Note that only the topic and payload survive transit.
Note that dat/tOut is a standard topic, so the attributes (units and title) would be added back in by a Handler Node.
- A special command cmd/sync can be sent to a nodes message handler asking it to publish a full JSON object for a device (or devices), including all data groups, values, and attributes. The command payload is an MQTT topic including wildcards, e.g. local/# (all), or +/+/boiler1/#. The reply for each device that matches is sent on the corresponding topic, e.g. myNetwork/node123/boiler1/json/sync and can be handled by a receiving system.
- Packaging a message as a JSON object, value and attributes, and send this instead of just the value. A receiving system can work out the payload is JSON and handle appropriately.
Node-RED Global Objects
Data stored in global objects is held in processor memory and not on disk.
The current data can be viewed within Node-RED in the data explorer.
network -> device -> group -> key
e.g. a message with a topic myNetwork/node123/myDevice/dat/outputTemperature would be stored in (global).readings.myNetwork.myDevice.dat.outputTemperature.value
Internally, message topics can be truncated and the network and node will be filled in. The data group will be assumed to be "dat" if not supplied, representing operational data.
e.g. a message with a topic setpoint would be stored in (global).readings.local.myNode.dat.setpoint.value
The following code could be used to read data and its attributes for output.
var localNetworkId = global.get("localNetworkId");
var node = global.get("node");
var reading = global.get("readings." + localNetworkId + "." + node + ".dat.outputTemperature");
var output = "The value of " + reading.title + " is " + reading.value + reading.units;
// "The value of Output Temperature is 35°C
Settings have a type, may have maximum and minimum values, units and a title. Certain types require additional fields such as select from a list settings.
Standard settings include:
- title (system title / name)
- io (system input/output configuration in JSON format)
- postCode (UK Postal Code)
- latLong (comma separated latitude and longitude)
- email (comma separated list of email addresses for alarms and reports)
The snapshot below shows a variety of setting types including numeric/text values, html, or JSON objects and arrays.
Links
- https://github.com/mcci-catena/docker-iot-dashboard A GitHub project using similar architecture for monitoring LoRaWAN devices.